What Micro Segmentation Is Not…
NSX-vSphere Micro Segmentation Review
NSX for vSphere has a compelling use case around Micro Segmentation –
- The ability to orchestrate the provisioning of new Layer 2 and Layer 3 application networks via API in a matter of seconds using VXLAN as the overlay technology allowing networks to be created for each application segment on demand. There are numerous benefits in doing this but the big one is this really simplifies the mobility of applications for BC/DR purposes… Easy to move the application and its dedicated network vs dealing with the complexity of splitting Layer 2 networks that support many applications.
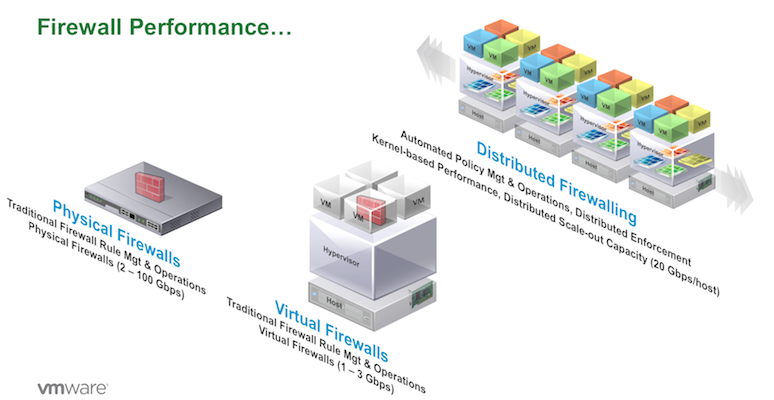
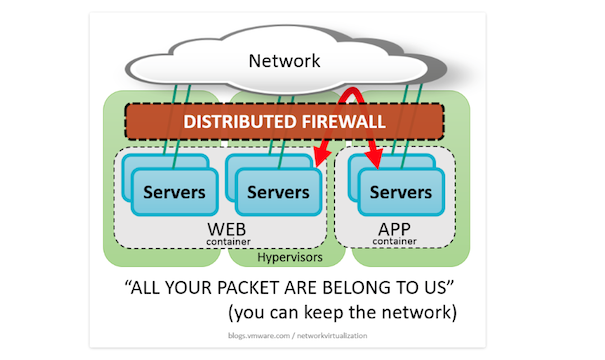
- The ability to isolate VM’s from each other using customer defined business attributes or vCenter attributes independent of the network topology using Layer 4 Stateful firewall policy. Even with VM’s on the same network segment as each other, Layer 4 Stateful firewall policy dictates how these VM’s should communicate with each other and to the outside world… If you want complete isolation of VM’s on the same network as each other, this is easily accomplished with Layer 2, 3, or 4 security policies.
- The ability to apply static or dynamic policy based on changing security conditions within the infrastructure. As example, a virus is identified or intrusion detected will automatically firewall protect the infrastructure from the compromised VM.
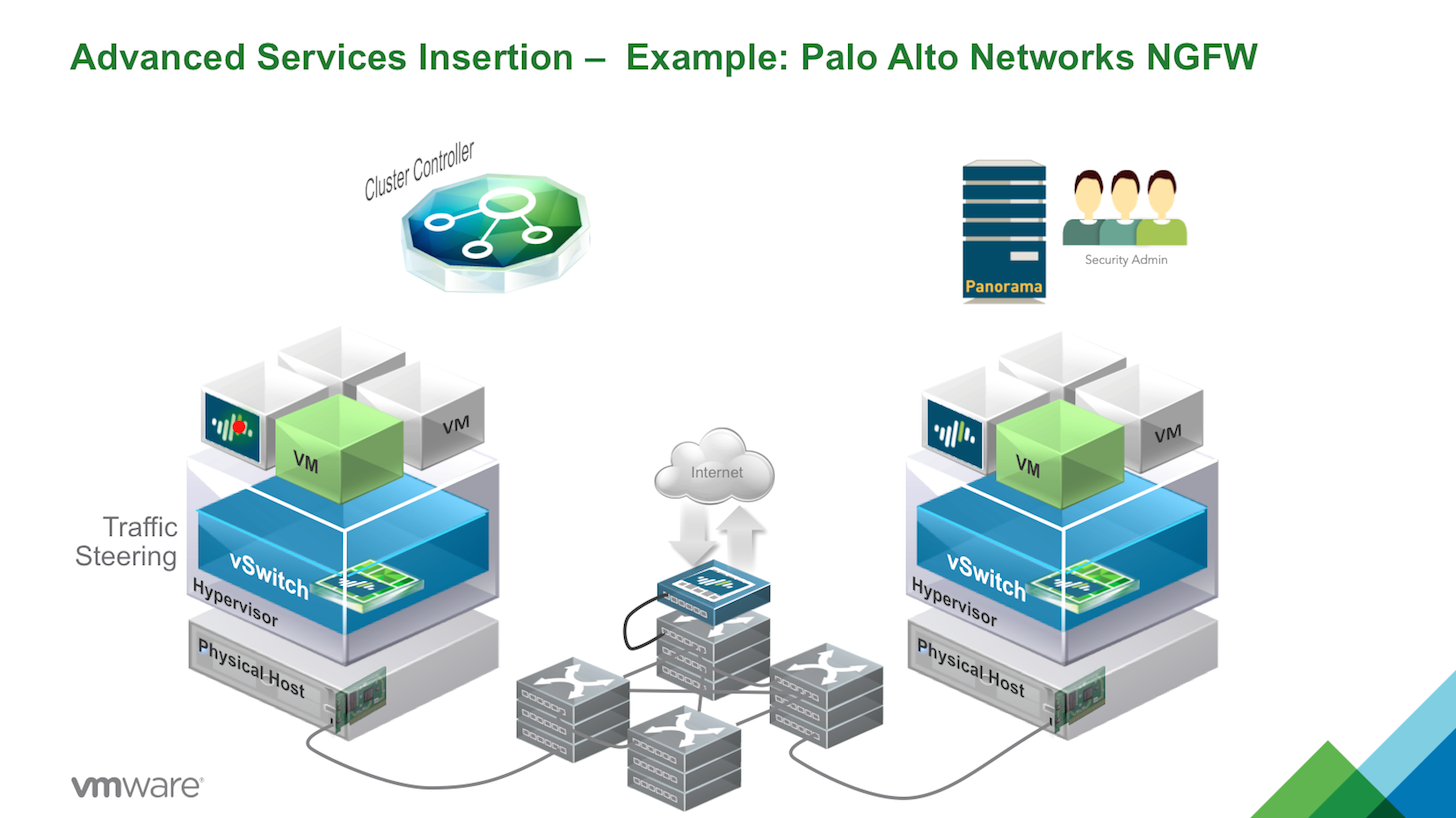
- Using 3rd Party extensibility, ability to extend native Layer 4 Stateful inspection to Layer 7 Deep Packet Stateful inspection…