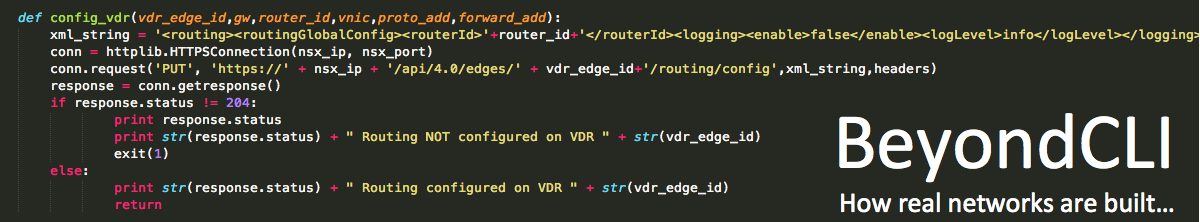
NSX L2VPN within the Data Center
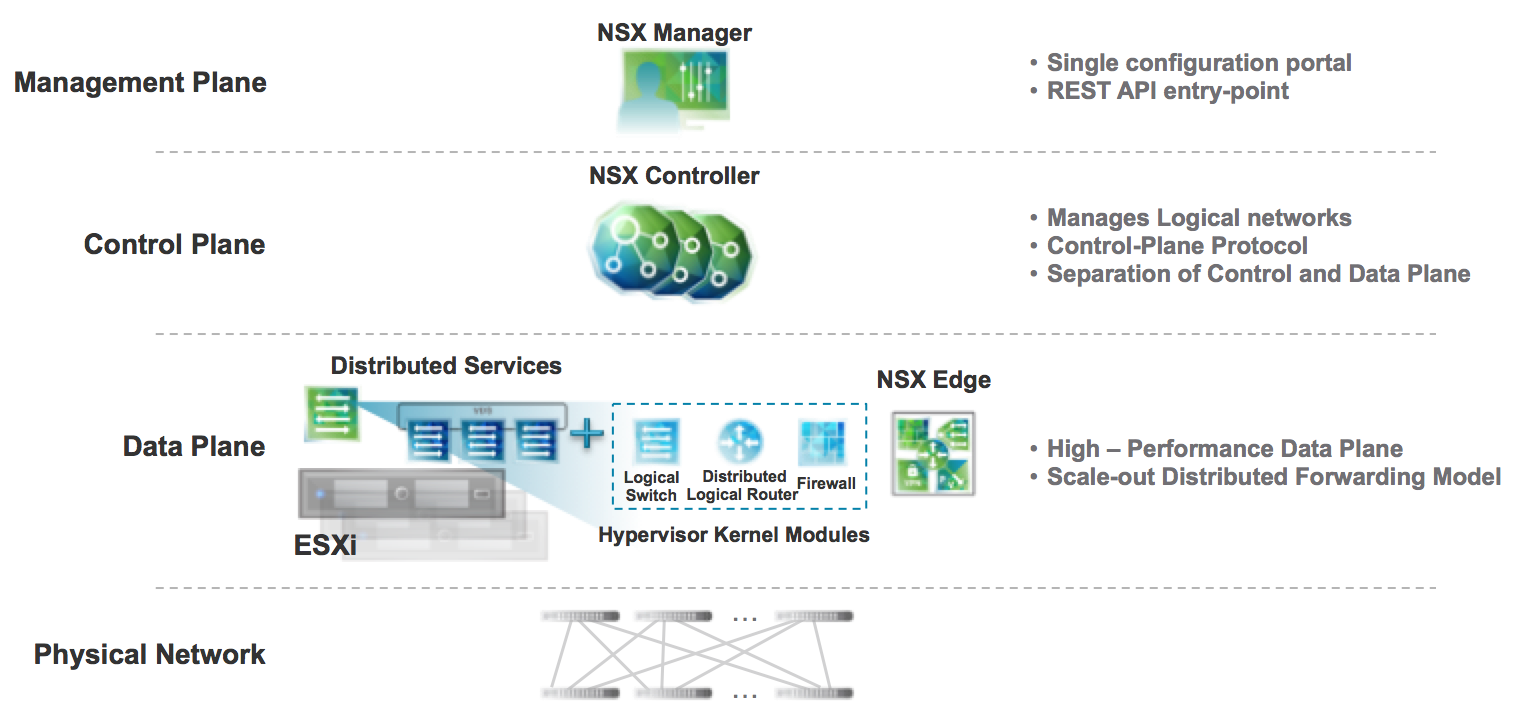
NSX Edge Services Gateways (ESGs) are deployed to perform various network functions (Network Function Virtualization) in an NSX environment.
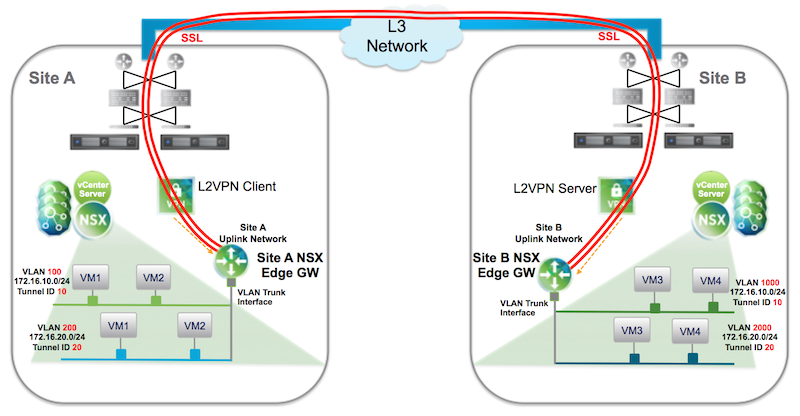
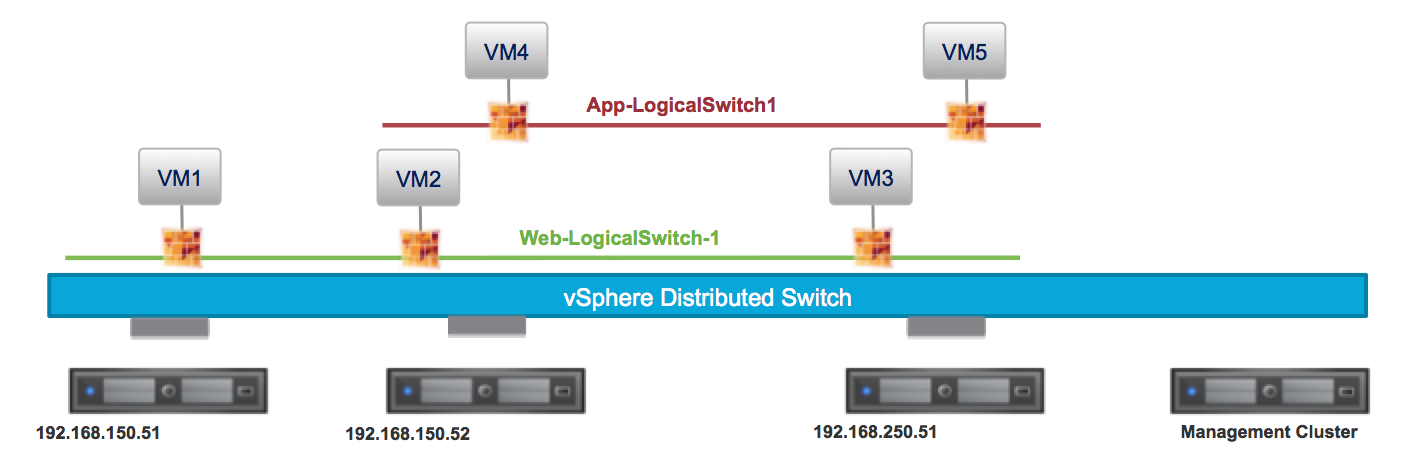
ESG’s deployed configured for L2VPN provide Layer 2 network adjacency between data centers allowing VLANs – VLANs, VLANs – VXLANs, and VXLANs – VXLANs to be bridged across a Metro Area or Wide Area Network.
The primary use case for L2VPN Edge Services Gateways is Private Cloud to Private Cloud and Private Cloud to Public Cloud Layer 2 LAN/VXLAN extension, but they are also a useful tool for VM mobility within a data center…