VeloCloud Event Log to Splunk
Recently announced is the ability for VeloCloud Edges to send Syslog to your favorite syslog server. This is a welcome feature to the VeloCloud product but there are some events that occur in the VeloCloud Orchestrator that are not Edge specific. Today we will demonstrate the use of the VeloCloud REST API and Splunk Modular Inputs to pull the VeloCloud Orchestrator Event Log data into Splunk…
VeloCloud Orchestrator (VCO) is the centralized UI for managing a VeloCloud SD-WAN solution. VCO was written ground up with an API and the UI was written to consume the API, thus all VCO capabilities are available via the documented REST API.
Three considerations when using the VCO REST API are:
- The only verb used by VCO REST API is POST… All activities that commonly would be associated with verbs GET, PUT, PATCH, DELETE are performed with the POST verb.
- API authentication is initially performed using a username and password which generates a session cookie. You pass the session cookie on subsequent API requests. The session cookie “normally” lasts for more than 24 hours but some VCO implementations set this to a smaller value.
- Responses are in JSON format.
There are other blogs on how to use the VCO REST API and I recommend the use of Postman to test API calls and validate responses…
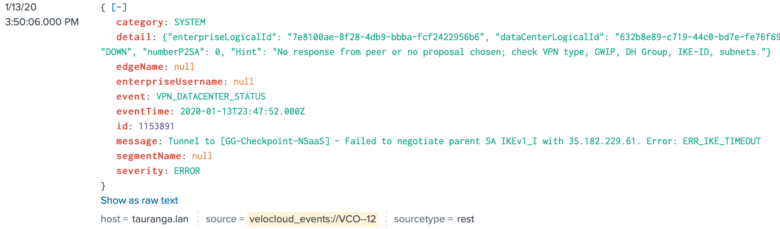
VCO Event Log
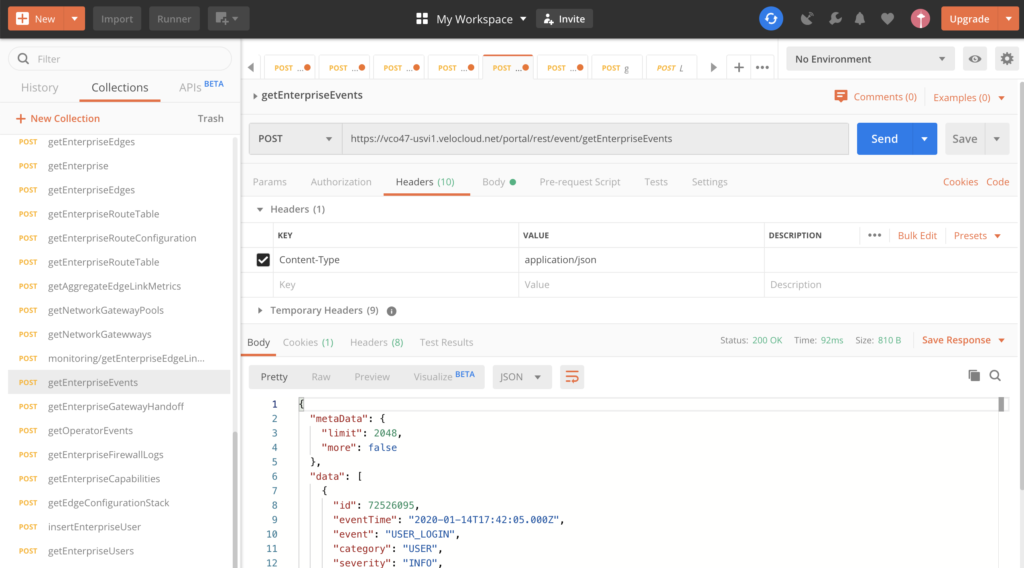
The specific URI request to pull the event log is as follows:
POST URI:
https://<vco url>/portal/rest/event/getEnterpriseEvents
Cookies:
A valid velocloud.session cookie from a previous authentication request.
Headers:
Content-Type = application/json
Body:
{}
or interval start and end times specified in the following format:
{'interval': {'start': '2020-01-14T00:50:06.554760Z', 'end': '2020-01-14T01:10:06.597254Z'}}
Response:
{
"metaData": {
"limit": 2048,
"more": false
},
"data": [
{
"id": 72451477,
"eventTime": "2020-01-14T00:00:07.000Z",
"event": "USER_LOGIN",
"category": "USER",
"severity": "INFO",
...
Splunk
My initial attempts at Splunk / VCO integration were to use a “common” Splunk Plugin that supports REST Modular Inputs and unfortunately, I ran into several problems –
- An issue with cookie passing that appears to be inherent in the Python “requests” library.
- The need to save the cookie for subsequent API calls together with tracking the age of the current cookie.
- The need to track the last log record written.
Modifying the REST Modular Inputs code to mitigate the above three issues added complexity to the code and thus a rewrite was needed…
Splunk Modular Inputs
Considerable documentation. and blog articles have been written on how to create Splunk Modular Inputs but unfortunately much of it is based on earlier versions of Splunk… The following links are for current versions of Splunk:
https://docs.splunk.com/Documentation/Splunk/8.0.1/AdvancedDev/ModInputsIntro
https://www.function1.com/2016/08/splunk-modular-inputs
https://docs.splunk.com/Documentation/Splunk/latest/Admin/Listofconfigurationfiles
Additionally, password encryption and state store are covered here:
https://www.function1.com/2017/02/encrypting-a-modular-input-field-without-setup-xml
http://www.georgestarcher.com/splunk-stored-encrypted-credentials/
https://splunkbase.splunk.com/app/282/
https://splunkbase.splunk.com/app/1621/
The VeloCloud Event Log Splunk Modular Input
TA_VeloCloud is a Splunk Modular Input which performs the following –
- Polls the VeloCloud SD-WAN Event Log for an Enterprise based on a specified interval (in seconds). Default is 300 seconds.
- Saves and encrypts the VCO Password or API Token.
- Saves and encrypts the VCO session Cookie or use the API Token.
- Checkpoints the time of the last log record written.
- Checkpoints the id of the last log record written.
- Cookie refresh interval (hours) can be set from 0 to 24 hours. Default is 8 hours.
- Code incorporates third party libraries as python source and not python EGG format.
Download the Modular Input Plugin from here:
https://github.com/djsincla/TA_VeloCloud
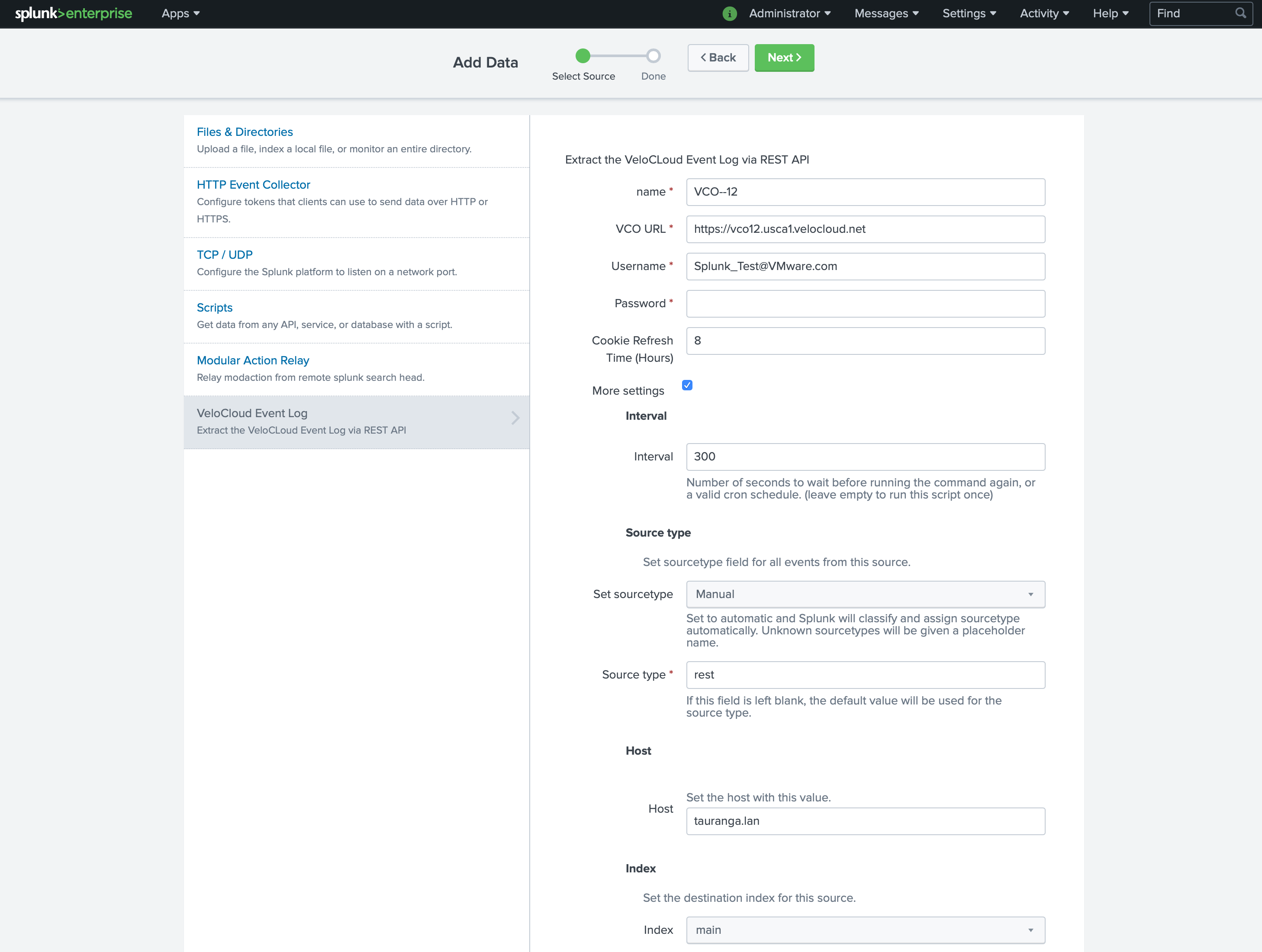
TA_VeloCLoud Configuration
Once installed, VCO Event Log poll configuration is as follows:
Name – The name given to this Modular Input. It is recommended to give it the name of the VeloCloud Orchestrator and Enterprise.
VCO URL – The https URL of the VeloCloud Orchestrator.
Username – An enterprise account user name for the environment you want to monitor. Operator accounts are not supported.
Password or API Token – Matching password or API Token for the VeloCloud Orchestrator username.
Optional values are:
Cookie Refresh Time – Successful authentication to VeloCloud Orchestrator (VCO) using a userid and password returns a session cookie which is used for subsequent API calls. Setting this value between 0 and 24 hours is a maximum interval between VCO reauthenticating for a new session cookie. Setting this value to 0 forces the Modular Input to request a session cookie every time the event log is read. If something was to happen to VCO (DR activity etc), modifying the modular input to set this value to 0 then back to a high value is a simple way to regenerate and save a new session cookie. Default is 8 hours.
More Settings – Exposes additional configuration options.
Interval – Polling interval in seconds between requests to the VeloCloud Orchestrator for event log data. Default is 300 seconds. Minimum is 120 seconds.
Source type, Host, and Index options are Splunk environment specific. Your Splunk administrator will recommend appropriate setting to use.
Update: As of July 2021, code has been validated against latest versions of both Splunk and VeloCloud Orchestrator.
Three versions of code are available –
Master – Splunk Python 2.x and VCO Userid and Password.
Python3 – Splunk Python 3.7+ and VCO Userid and Password.
Token3 – Splunk Python 3.7+ and VCO API Token.
Enjoy!