NSX vSphere Service Composer – Part 1 – Canvas and Security Groups
When reviewing NSX vSphere for the first time, it’s easy to see the value of the kernel based distributed routing, switching, and firewall capabilities, combined with Network Function Virtualization (NFV) of features such as Load Balancing, SSL VPN, and DHCP, but Service Composer capabilities “out of the box” seem unclear…
NSX Service Composer provides four major capabilities –
- The definition of network tenancy and sub tenant environments within an SDDC.
- The definition of application security requirements within an SDDC.
- 3rd party partner integration definition.
- Dynamic security automation in conjunction with 3rd party partner integration.
These capabilities allow network policy to be easily organized (how you want to protect) and services can be easily mapped to resources (how you want to protect them) for consumption in the SDDC. Service Composer provides the automation of network security across your environment.
Although I am detailing vSphere Web UI screenshots, everything in Service Composer is available via the RESTful API which I will detail at the end of this post.
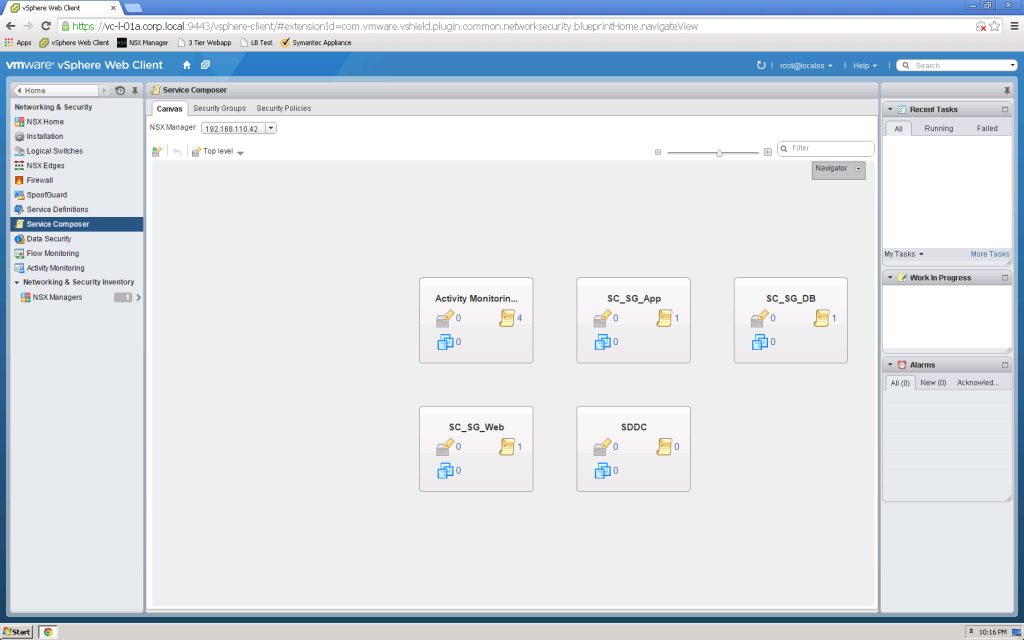
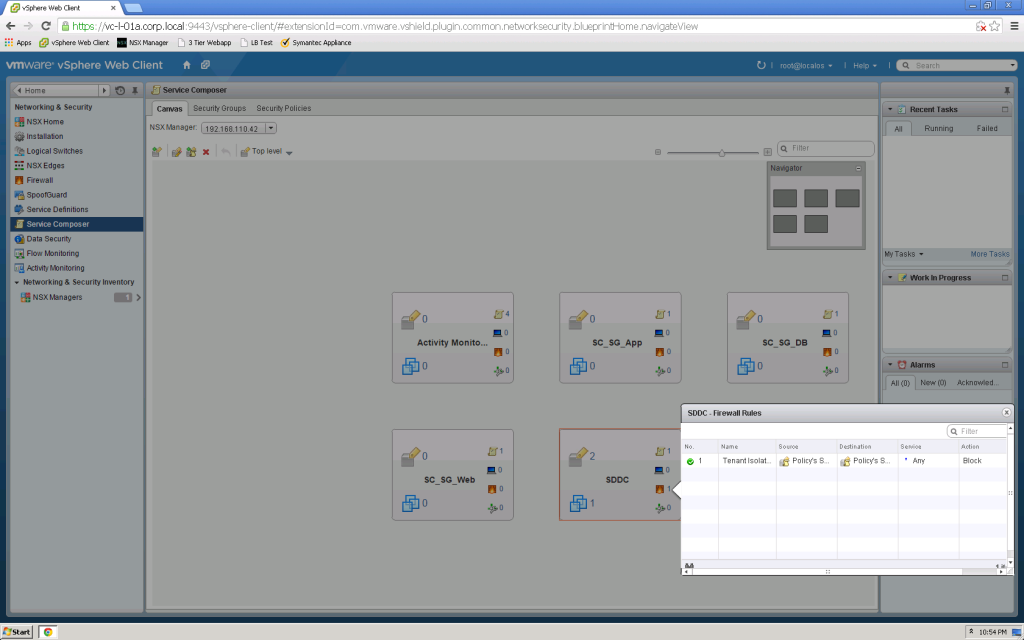
Service Composer Canvas
Service Composer Canvas is the working environment showing all Service Composer definition and relationships between the various definitions…
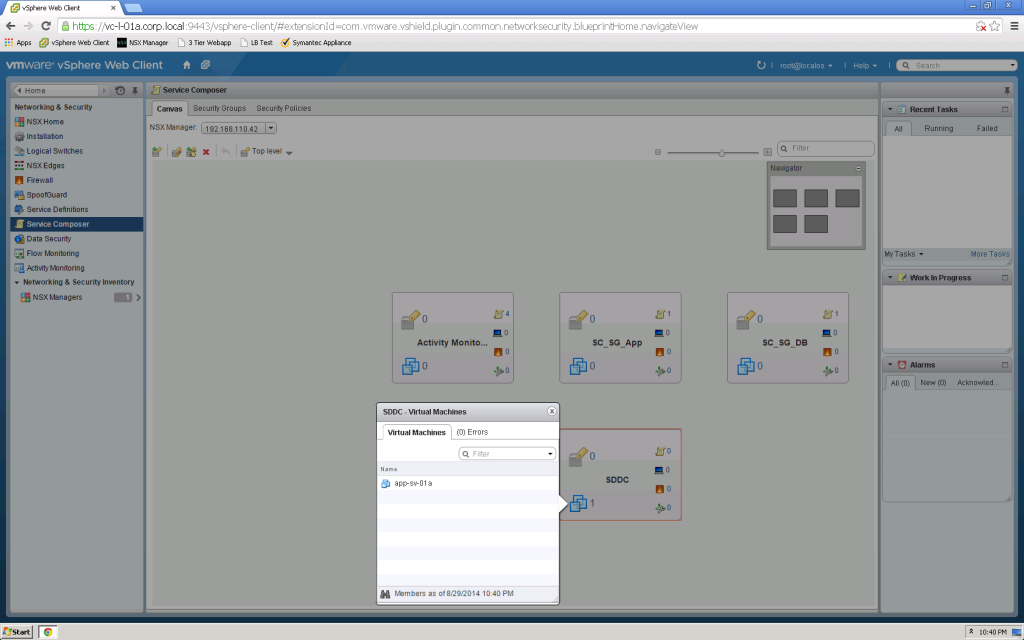
Each block on the Service Composer Canvas represents a Security Group definition which includes security policies, endpoint services, firewall rules, network introspection services, virtual machines, and included security groups (Security Group nesting).
It is the Security Group nesting that provides a framework for a multi dimensional security model across your SDDC.
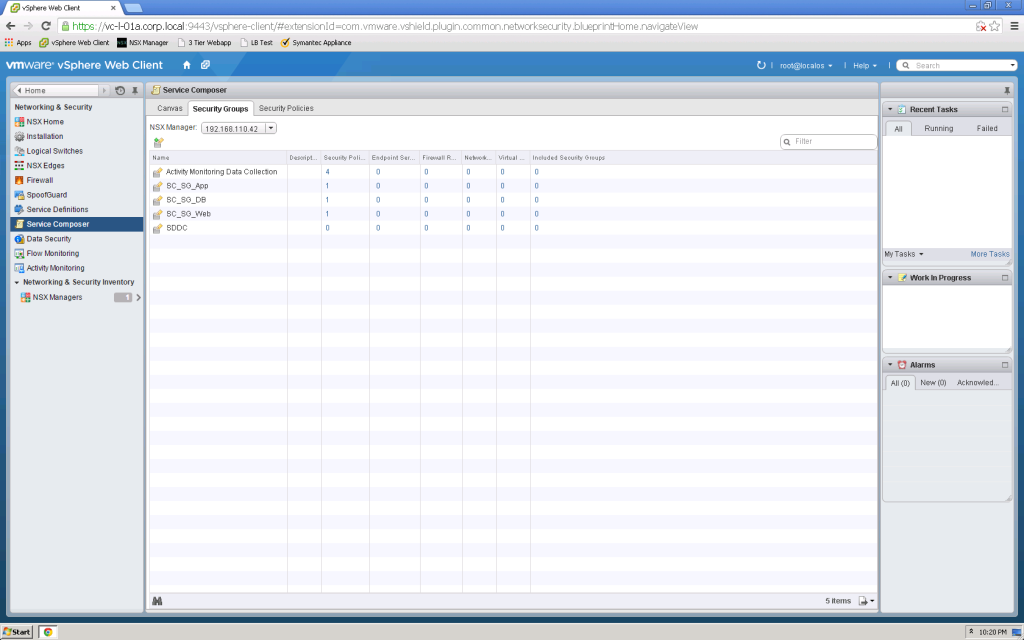
The Security Groups tab provides a simple display detailing the rules that are applicable to your environment…
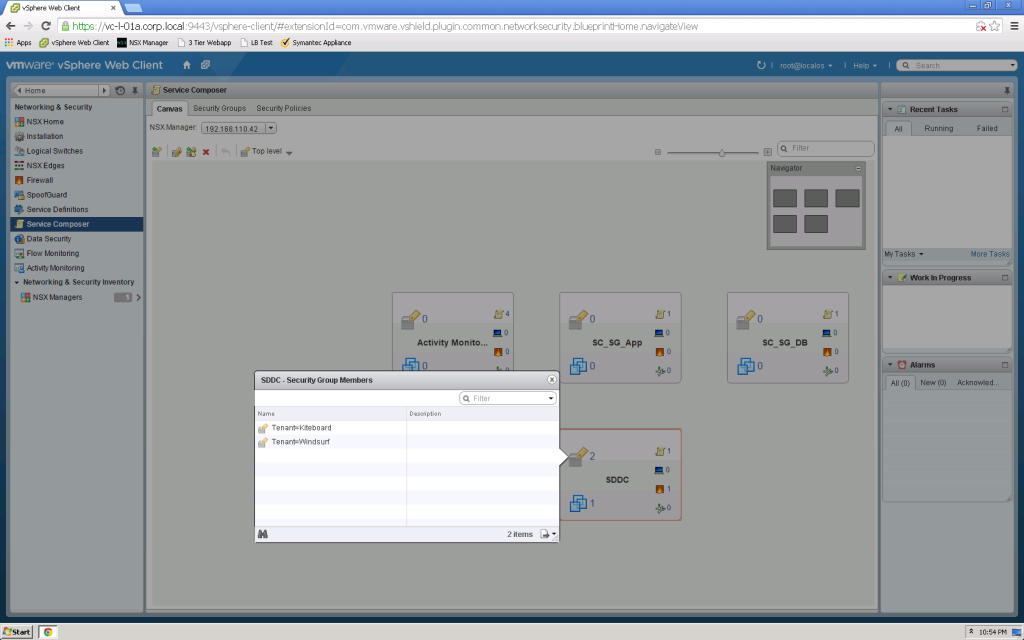
Static and Dynamic Security Group Membership
Service Composer uses vSphere Constructs such as Cluster Name and VM Name for static and dynamic membership.
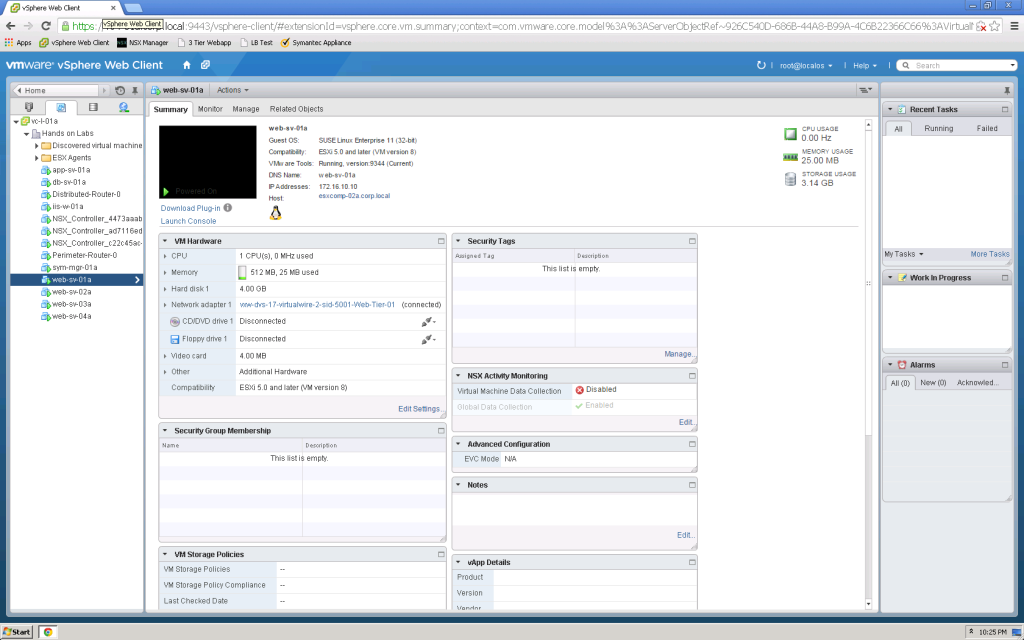
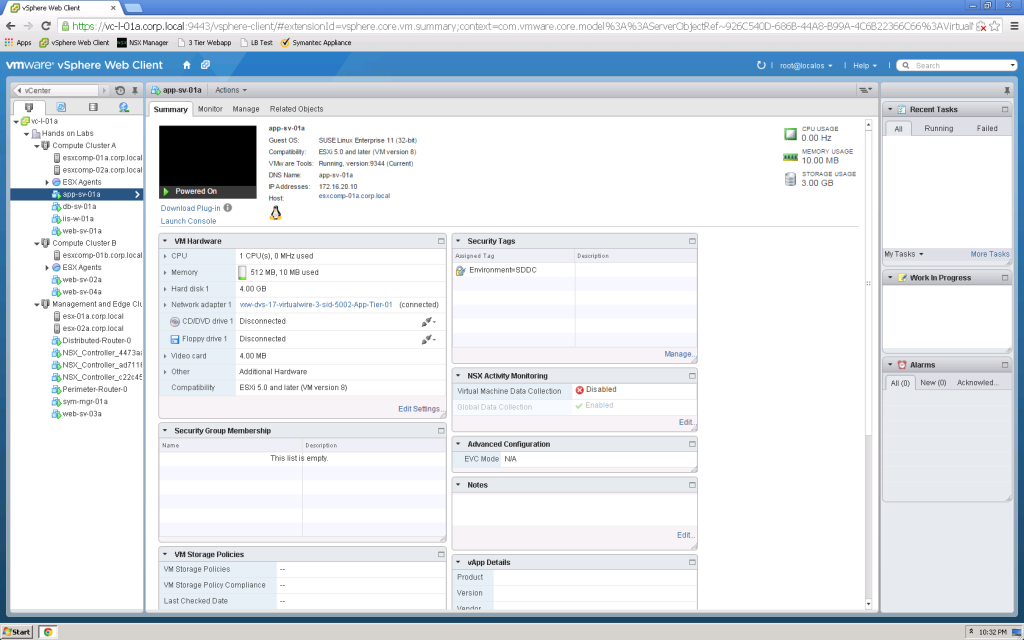
One of the most powerful features of the NSX Distributed Firewall and Service Composer is the automated application of security based on the static or dynamic application of Security Tags to vSphere Virtual Machines.
With the implementation of NSX, the vSphere UI is expanded to add Security Tags to Virtual Machine configuration…
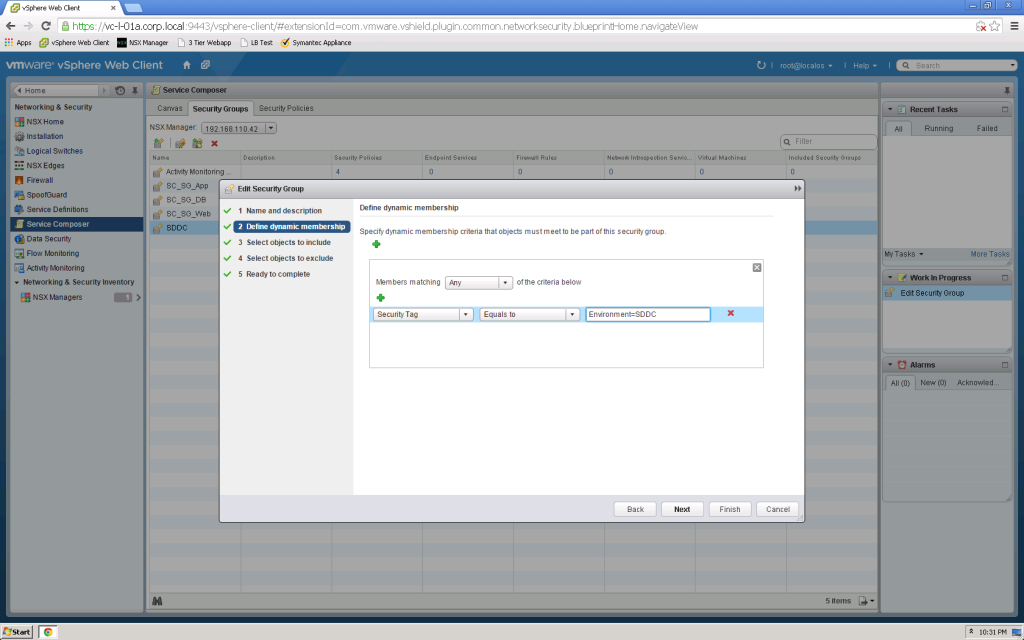
Service Composer Security Group definition allows you to specify the rules for inclusion… In this example, I will add a dynamic membership Security Tag rule to the SDDC Security Group… Rule says “Environment=SDDC”…
Added “Environment=SDDC” to VM…
And Security Group automatically updates to include VM…
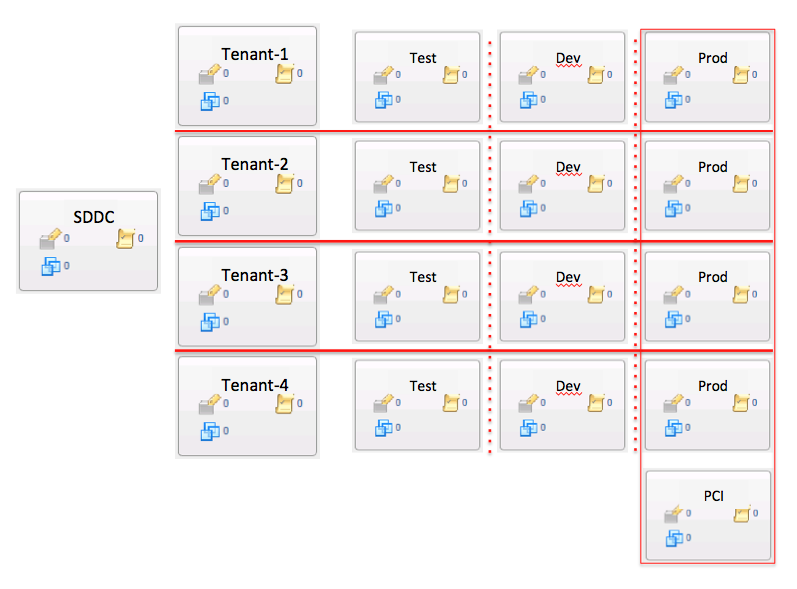
Network Tenant Rules
The definition of nested Security Groups allows for the definition of Tenant to Tenant rules (access restricted), and sub tenant environment rules (access limited)…
Essentially, the complete definition of a Multi Tenant SDDC can be created using the Service Composer Security Groups and associated Firewall Rules, leveraging vSphere and NSX constructs.
The following is an example of what can be built with Service Composer, and Service Composer can easily support additional dimensions such as PCI and other constructs independent of tenant topology…
NSX vSphere Service Composer API
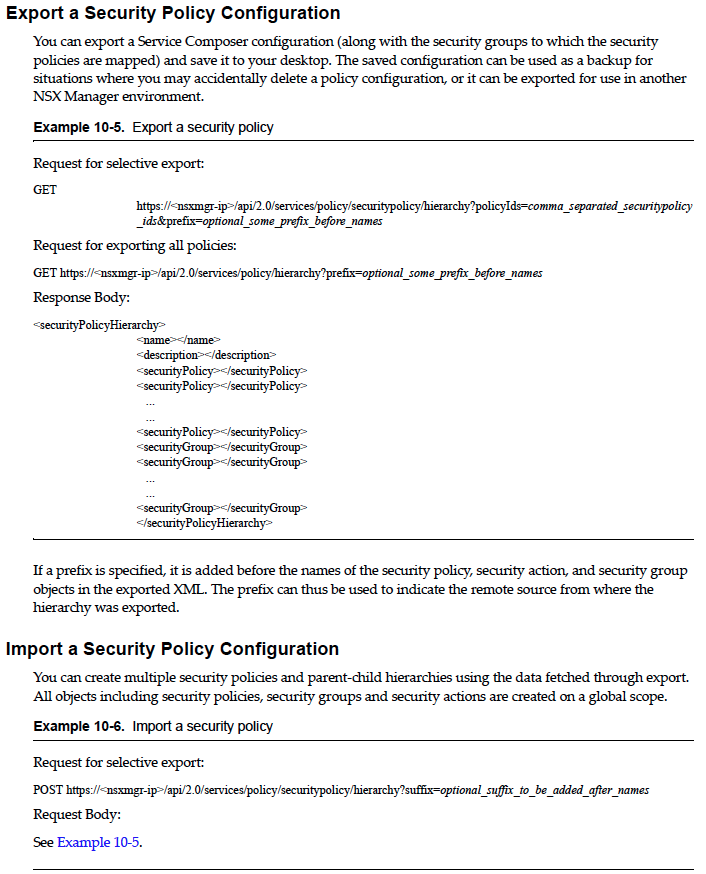
The NSX vSphere 6.0 API Guide details all of the REST API calls available including the Service Composer REST API calls. Probably the most important API calls for Service Composer are the two API calls to allow you to export and import your SDDC security policy definition.
You can easily recreate your SDDC security policy for BC/DR reasons or just share your SDDC Security Policy with your industry peers 😉
IMO, I believe there is an opportunity for an open community ecosystem to be built around sharing Service Composer tenant and application profiles – Certainly, the import and export capabilities of Service Composer allow for this capability.
As a followup, I’m going to find some great examples of SDDC Network Tenancy and share with you. Part 2 will focus on Application Security!